PHOTOGRAMMETRIC ENGINEERING & REMOTE SENSING
September 2019
625
GIS
&
Tips Tricks
By Al Karlin, Ph.D.,CMS, GISP
B
y now, just about everyone has experienced a phishing,
spear phishing, or pharming attack. We have all been
exposed to various scamming emails and phone calls,
and we have all persevered through countless hours of IT
training and testing. But how many of you have had your
electronic image or lidar files tampered with by unscrupulous
individuals? Believe it or not, I have encountered cases
where an image file distributed through public records has
been altered, and then claimed to be the original. How do
you establish a legal chain-of-custody and prove the file to be
altered? The answer is…secure hash algorithms (SHA).
SHAs are a family of cryptographic hash functions that were
originally published by the National Institute of Standards
and Technology as a U.S. Federal Information Processing
How Safe Are Your Files, Anyway?
Standard (FIPS). The SHA-1 family of algorithms takes an
input file, sometimes referred to as a string or value, and
generates an “almost unique” 160-bit (20-byte) hash value,
known as a message digest, that is typically rendered as a
hexadecimal number and is 40 digits long. Since 2010, the
original SHA-1 algorithms have been updated to SHA-2 and
SHA-3 algorithms with 256-bit and/or 512-bit hash values.
The general procedure to protect your image, or lidar or
geographic information systems (GIS) files would be to select
several algorithms from the family, calculate multiple SHA
values for your files, and store those away for safe keeping.
Then when you distribute the file, you do not distribute the
hash codes, so if or when a file is altered, you recalculate the
hash codes on the “altered” file, and if or when the new codes
do not match the codes on file, you
have the chain-of-custody to indicate
tampering.
While this may not seem significant,
I have experienced cases where an
image file was distributed to a public
client. The client modified the file to
remove endangered plant species,
claimed that the plant species were
never on the parcel, and proceeded
to destroy the plants. The case was
adjudicated by fining the client when
the hash codes on file did not match
the hash codes generated from the
client’s files.
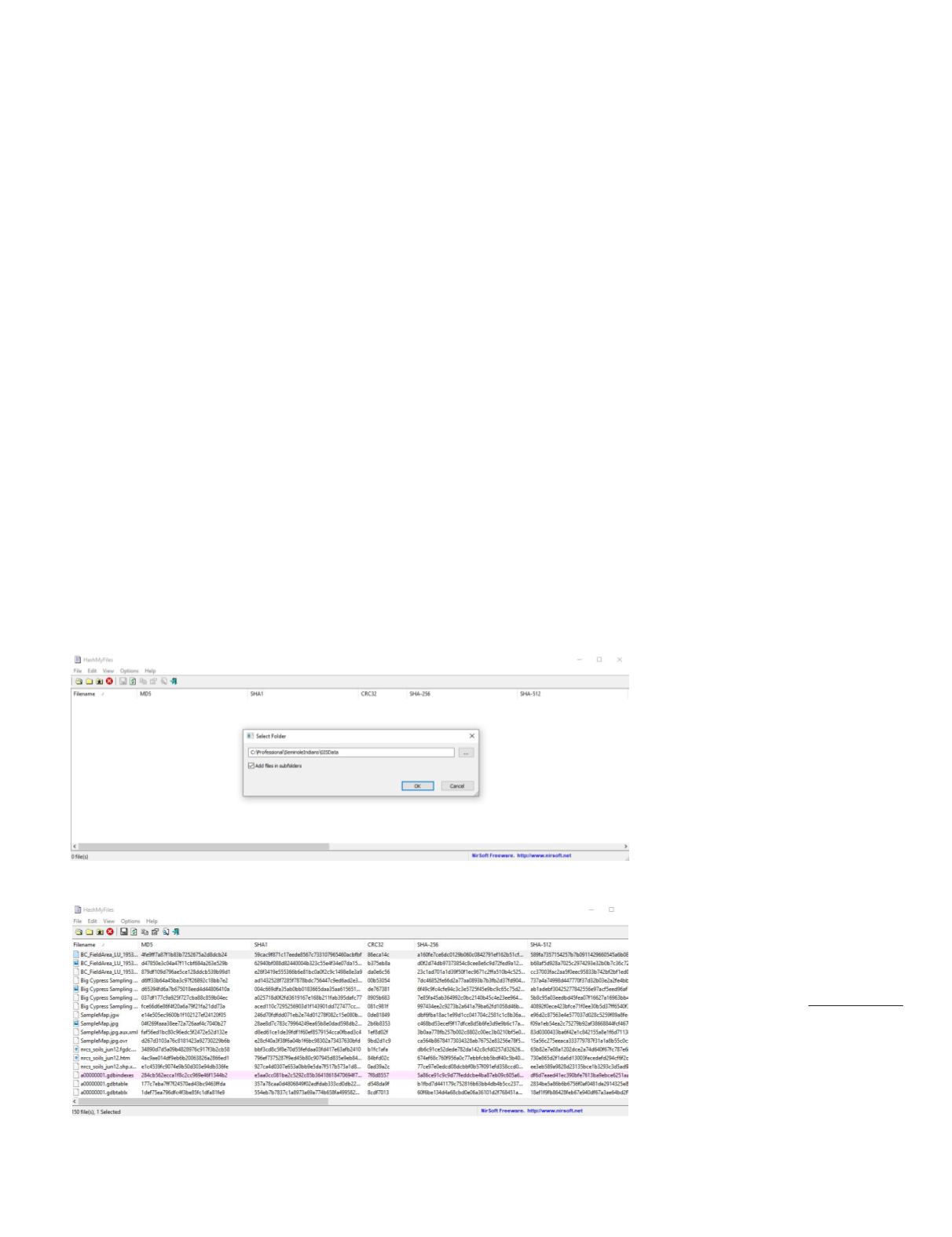
Hashing individual files and/or
entire directories can be accomplished
with a small freeware executable from
NirSoft Inc.
The Nirsoft software on a Xeon 3.2GHz processor took a little less than two minutes to
generate the six hash codes and record the file parameters.
Once the hash codes are generated, it is a simple matter of “Select All” (CTRL-A), copy
(CTRL-C), and paste (CTRL-V) into an Excel spreadsheet template.
Photogrammetric Engineering &
Remote Sensing
Vol. 85, No. 9, September 2019, pp.
625–626.
0099-1112/19/625–626
© 2019 American Society for
Photogrammetry and Remote Sensing
doi: 10.14358/PERS.85.9.626


